top of page


Firmware Security Playbook for MedTech Manufacturers
Medical device manufacturers already operate under intense pressure to meet safety, quality, and regulatory requirements. Cybersecurity adds another layer of responsibility, especially when it comes to firmware updates. Hospitals rely almost entirely on manufacturers to keep devices secure, and doing this well requires clear guidance, predictable processes, and practical tools. This playbook is meant to help. It outlines why firmware security has become a manufacturer's respo
Rajesh Kanungo
Dec 16, 20253 min read
10 Ways to Gain Hospital Trust Through Device Security
Why Device Security Must Be a Manufacturer Priority Today’s medical devices are tightly connected to hospital networks, clinical systems, cloud platforms, and remote support tools. This improves patient care, but it also opens the door to cyber threats. If your device has a vulnerability, hospitals expect you to take the lead. One unpatched or misconfigured device can cause: Workflow disruptions and clinical downtime Delayed diagnoses or treatments Exposed patient data Hospit
Rajesh Kanungo
Dec 10, 20256 min read


Managing Cybersecurity as a CAPA Event: 5 Steps to Handle Risks Effectively
Cybersecurity incidents are increasingly recognised as quality and compliance events that can affect the entire organisation, rather than being limited to the IT department. Because a single vulnerability could disrupt operations, compromise product integrity, or lead to regulatory noncompliance, cybersecurity issues must be handled with the same rigor as other CAPA events. When an organisation combines cybersecurity risk management (AAMI TIR57:2016 (R2023)) with safety and o
Rajesh Kanungo
Nov 25, 20254 min read
Top 10 Holiday Cybersecurity Risks and How to Stay Safe
The holiday season brings an extra level of excitement, with some free time to enjoy and relax, so it's no wonder many consider it one of the busiest times of the year. It often brings increased online activity, from shopping and banking to coordinating travel and sharing with friends and family. Cybercriminals know this fact and use it to take advantage of the busy season. Cybercriminals use the holiday season to target individuals and organizations through scams, phishing
Rajesh Kanungo
Nov 18, 20255 min read
After the Breach: Rebuilding Trust and Resilience in Medical Devices
A 10 Point Framework for Responding to a Breach Connected medical devices have transformed patient care, but with connectivity comes exposure. Cyberattacks on medical device manufacturers now pose not only data privacy risks but also patient safety and regulatory consequences. When a breach occurs, the damage extends far beyond compromised systems. It strikes at the heart of what matters most: trust. Rebuilding that trust requires swift, transparent, and disciplined action gr
Rajesh Kanungo
Oct 23, 20253 min read
Rebuilding Patient Trust After a Data Breach in a Rural Hospital
10 Key Actions Every Rural Hospital Can Take A cyberattack at a rural hospital doesn’t just shut down systems; it shakes the very foundation of trust that keeps your community coming through your doors. In towns where patients know their nurses, doctors, and front-desk staff by name , a data breach feels deeply personal. It’s not just information that’s been exposed; it’s a relationship that’s been damaged. According to the National Rural Health Association, 60% of rural hos
Rajesh Kanungo
Oct 9, 20253 min read
Legacy Medical Devices: Tackling Cybersecurity Concerns
Under the FDA’s updated rules (Section 524B of the FD&C Act), any medical device that includes software, connects to a network, or could...
Rajesh Kanungo
Sep 16, 20252 min read
Legacy Systems and Cybersecurity: What Rural Hospitals Need to Do
In today’s rapidly evolving healthcare landscape, legacy systems in rural healthcare systems are still common. A 2021 Healthcare...
Rajesh Kanungo
Sep 9, 20252 min read
How to Protect Your Medical Devices and Your Business in 2025
Cybersecurity is no longer optional for medical device companies. New FDA requirements, tougher hospital IT standards, and rising cyber...
Rajesh Kanungo
Aug 12, 20252 min read
2025 Cyber Updates: FDA 2025 Cybersecurity Update for Medical Device Manufacturers
The FDA released a revised guidance titled “ Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket...
Rajesh Kanungo
Aug 6, 20251 min read
Stretching Every Dollar: Smart Strategies for Rural Hospitals
Rural hospitals are the backbone of healthcare in underserved communities, delivering everything from primary to long-term care for over...
Rajesh Kanungo
Aug 4, 20252 min read


Securing an AI System - Tutorial - Part 1
Methods to defend against data poisoning attacks Saurabh Malpure (TalaSecure, Inc.) Rajesh Kanungo (TalaSecure, Inc.) Jaime Burks (UCSD)...
Rajesh Kanungo
Aug 21, 202423 min read


GenAI Security Challenges and Solutions
Rajesh Kanungo (CEO, TalaSecure, Inc.) Tejpal Chadha (CEO, MyAiDr.ai) Executive Summary Investment in Artificial Intelligence (AI) and...
Rajesh Kanungo
Jul 22, 202411 min read
512,000 Radiology patients' data stolen
Executive Summary Consulting Radiologists LTD. (“CRL”) reported that cybercriminals may have stolen the data of roughly 512,000 patients....
Rajesh Kanungo
Jun 21, 20242 min read
ARM Memory Security Broken
Executive Summary A team from South Korea, Juhee Kim, Youngjoo Lee, Jinbum Park, Taesoo Kim, Sihyeon Ro, Jaeyoung Chung, and Byoungyoung...
Rajesh Kanungo
Jun 18, 20242 min read


Risk Management, Data Loss Prevention and everything around it…
The first in a series of blog posts about how Security Risk and Data Loss Prevention are related.
Rajesh Kanungo
Sep 17, 20224 min read
Cryptocurrency: the US tries to legitimize it
The latest White House development in cryptocurrencies, Executive Order (EO)on Ensuring Responsible Development of Digital Assets, is...
Rajesh Kanungo
Mar 9, 20222 min read


Ransomware: how to estimate the Risk
Why is it so hard to estimate cybersecurity, especially ransomware risk? Why is it that ransomware attacks have an outsized impact on an...
Rajesh Kanungo
Feb 21, 20223 min read


Cracking the password of an Apple Mac with a T2 Security Chip
Macs with Intel processors and Apple T2 Security Chip can now be broken into using simple brute force methods. A company, Forensic...
Rajesh Kanungo
Feb 17, 20222 min read

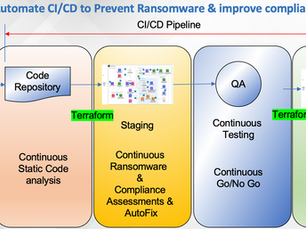
Prevent Ransomware: its in your CI/CD pipeline
Wouldn't it be nice if you rarely had to roll back your newly deployed changes to the infrastructure due to security compliance (SOC2,...
Rajesh Kanungo
Feb 16, 20222 min read
bottom of page