How to Protect Your Medical Devices and Your Business in 2025
- Rajesh Kanungo
- Aug 12, 2025
- 2 min read
Cybersecurity is no longer optional for medical device companies. New FDA requirements, tougher hospital IT standards, and rising cyber threats mean your devices must be secure to enter and stay in the market. Hospital IT teams are increasingly blocking sales over security concerns, and a single breach can delay approvals, damage trust, and hurt your bottom line.
In a previous newsletter, 2025 Cyber Updates: FDA Cybersecurity Update for Medical Device Manufacturers, we shared a brief overview of the FDA’s updated cybersecurity expectations.
Here’s a quick checklist to help you meet expectations and reduce risk.
1. Partner with Health Systems Early
Align with hospital cybersecurity and privacy expectations early, much before clinical trials.
Understand their workflows, remote access requirements, and preferences for cloud or on-premises solutions.
Use hospital security RFPs and security risk feedback as design inputs.
2. Tackle Ransomware and Insurance Risks
Perform formal ransomware risk assessments.
Engage cyberinsurance firms early to lower premiums through a strong risk posture.
3. Engage FDA Cyber Experts Proactively
Pre-submission meetings are critical; address FDA cybersecurity concerns before they become roadblocks.
4. Build a Cybersecurity-Ready Organizational Structure
Form postmarket surveillance teams.
Plan for patching, monitoring, and communicating vulnerabilities throughout the product life cycle.
5. Regulatory Must-Haves
Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions (2025).
Threat modeling across lifecycle stages (design, deployment, decommissioning).
Software Bill of Materials (SBOM).
Security risk metrics (e.g., patch timeframes).
Secure architecture diagrams and testing evidence.
6. Other Standards
IEC 81001-5-1: FDA-recognized standard for secure medical software.
NIST SP 800-218: Secure Software Development Framework.
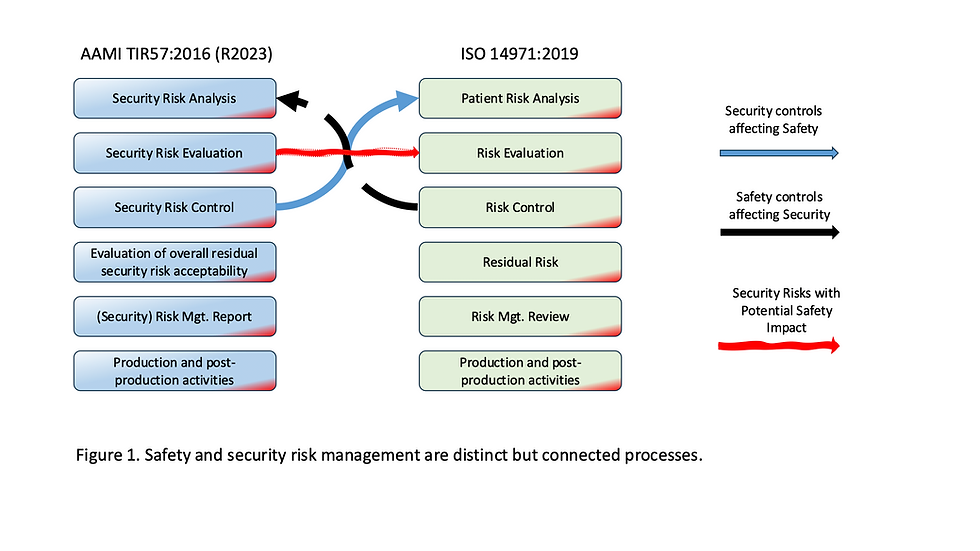
AAMI TIR57:2016 (R2023): Principles For Medical Device Security - Risk Management.
AAMI TIR97:2019 (R2023): Principles For Medical Device Security - Postmarket Risk Management For Device Manufacturers.
ISO 14971:2019: Medical Devices - Application of Risk Management to Medical Devices.
NIST SP 800-53 Rev. 5: Security and Privacy Controls for Information Systems and Organizations.
NIST Cybersecurity Framework 2.0 (NIST-CSF).
7. Postmarket Surveillance
Maintain source code security (e.g., escrow accounts).
Provide timely updates—not via USB!
Equip users with clear, accessible cybersecurity instructions.
Perform penetration testing and fuzzing regularly.
The senior management must champion a “security-by-design” culture, from concept to end-of-life, which can protect the reputation and lead to long-term profitability.

Comments