Firmware Security Playbook for MedTech Manufacturers
- Rajesh Kanungo
- Dec 16, 2025
- 3 min read
Medical device manufacturers already operate under intense pressure to meet safety, quality, and regulatory requirements. Cybersecurity adds another layer of responsibility, especially when it comes to firmware updates. Hospitals rely almost entirely on manufacturers to keep devices secure, and doing this well requires clear guidance, predictable processes, and practical tools.
This playbook is meant to help. It outlines why firmware security has become a manufacturer's responsibility, the challenges hospitals face, and how manufacturers can make updates safer and easier without adding unnecessary operational burden.
Why Firmware Updates Are Now a Manufacturer's Responsibility
Modern medical devices improve patient care, but when firmware updates are delayed, unclear, or risky to apply, they introduce real security exposure. Hospitals are not equipped to solve this on their own. If reliable update paths are missing, manufacturers often face increased regulatory attention, customer frustration, emergency fixes, and escalating support demands.
Predictable, secure, and easy-to-deploy updates protect patient safety, reduce downstream issues, and preserve trust.
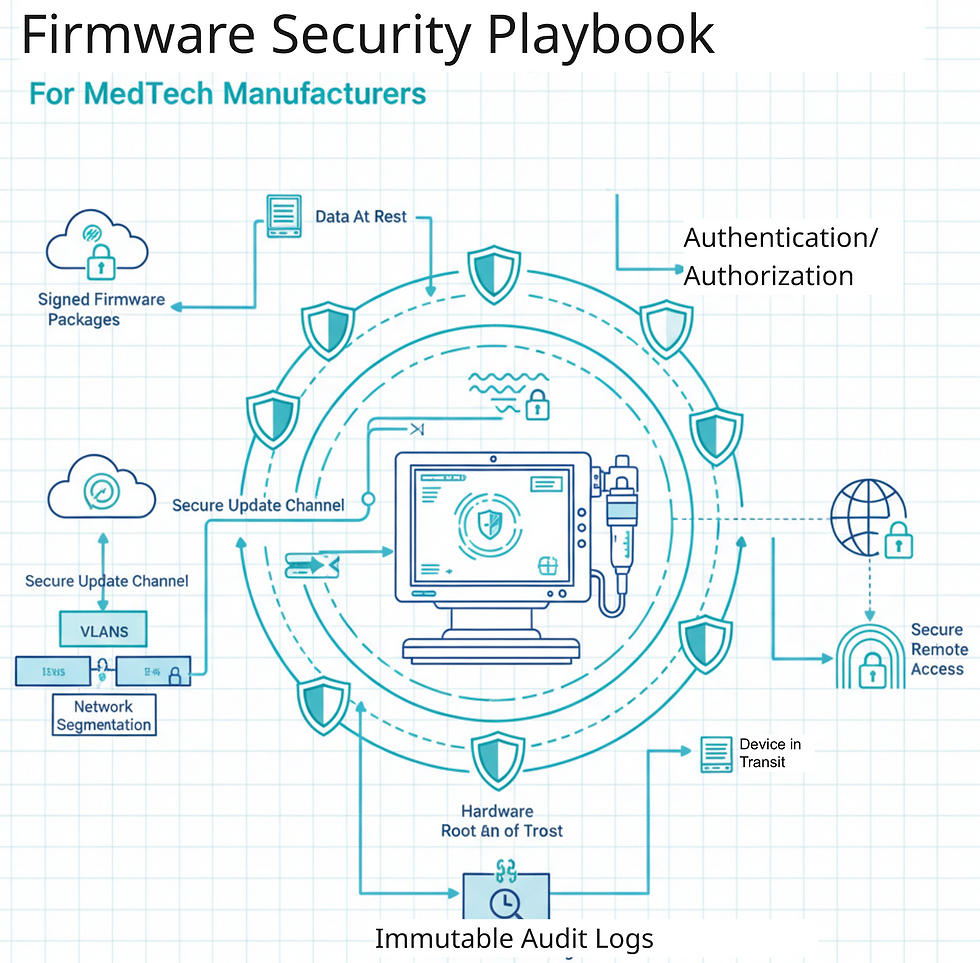
Why Firmware Security Breaks Down in Practice
Hospitals want to keep devices secure, but they often lack the information and tooling needed to do so safely. Common challenges include:
Firmware updates that are difficult to schedule, risky to install, or poorly documented
Mixed device fleets with different security capabilities
Unclear or unsecured vendor remote access pathways
Incomplete device inventory and metadata
These challenges are not failures on the hospital side. They point to areas where manufacturers can provide more explicit guidance and safer defaults.
What Manufacturers Should Provide to Support Hospitals
1. Predictable and Easy Firmware Updates
Hospitals need to know when updates are coming, how long they will take, and how to recover if something goes wrong. Clear schedules, signed packages, step-by-step instructions, and safe rollback options reduce hesitation and risk.
2. Strong Credentials and Access Controls
Devices should ship with unique credentials, role-based access, and options for stronger authentication where clinically feasible. Clear password guidance helps prevent simple but common security issues.
3. Clear Network Segmentation Guidance
Hospitals rely on manufacturer guidance to safely deploy devices on their networks. Providing required ports, protocols, VLAN guidance, and example architectures makes secure deployment far more achievable.
4. Secure Remote Support Models
Remote access should be time-limited, auditable, and protected with strong authentication. Removing always on or uncontrolled access paths reduces risk for both hospitals and manufacturers.
5. Built-in Encryption with Clear Documentation
Hospitals and regulators need to understand how data is protected. Encryption for data at rest and in transit should be enabled by default and clearly documented.
6. Accurate Device Identification and Metadata
Hospitals cannot protect what they cannot identify. Providing UDI information, MDS2 data, and discovery profiles enables better inventory, faster patching, and fewer blind spots.
7. Audit and Hardening Guidance
Hospitals face regular audits. Providing hardening guides, baseline configurations, and logging guidance helps them pass audits and reduces support escalations.
8. Short and Practical Training Materials
Training does not need to be heavy. Quick checklists, short videos, and simple do-and-do-not guidance significantly reduce avoidable incidents.
9. Clear Access Control Models
Defined roles, privilege boundaries, and audit guidance help hospitals manage access safely and consistently.
10. An Integrated Incident Response Plan
When something goes wrong, hospitals look to the manufacturer first. Clear steps for isolation, escalation, forensic support, and recovery reduce downtime and protect patient safety.
How Firmware Updates Should Be Delivered
Trust is often won or lost during updates. Manufacturers can improve outcomes by:
Communicating downtime and clinical impact clearly
Using signed packages and integrity checks
Explaining why an update matters and what risk it addresses
Supporting staged rollouts
Offering secure remote or OTA updates where appropriate
Supporting Manufacturers Through the Lifecycle
Strong firmware security is not about perfection. It is about reducing uncertainty, supporting hospitals, and building trust over time. Manufacturers who make updates predictable and transparent reduce support burden, regulatory risk, and customer friction.
If you are looking to simplify firmware security and make compliance more manageable, we are always happy to share what we are seeing across the industry and compare notes.
Comments