After the Breach: Rebuilding Trust and Resilience in Medical Devices
- Rajesh Kanungo
- Oct 23, 2025
- 3 min read
Updated: Oct 24, 2025
A 10 Point Framework for Responding to a Breach
Connected medical devices have transformed patient care, but with connectivity comes exposure. Cyberattacks on medical device manufacturers now pose not only data privacy risks but also patient safety and regulatory consequences.
When a breach occurs, the damage extends far beyond compromised systems. It strikes at the heart of what matters most: trust. Rebuilding that trust requires swift, transparent, and disciplined action grounded in both technical response and regulatory rigor.
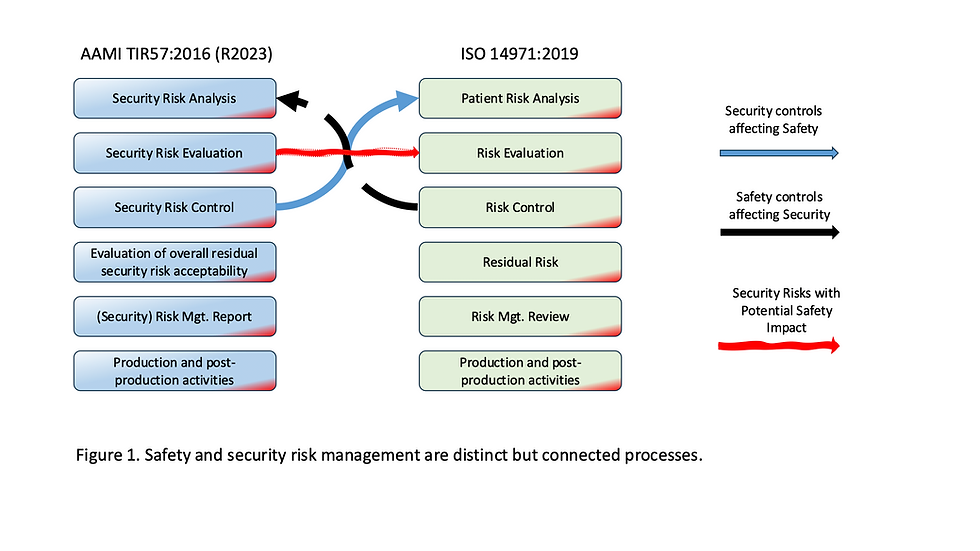
Below is an integrated 10-step framework to help medical device organizations recover confidently, in line with AAMI TIR57, ISO 14971, and FDA expectations.
Additionally, we will discuss multiple high-severity vulnerabilities in Oxford Nanopore Technologies’ MinKNOW sequencing platform.
⚡ 1. Immediate Response (First 72 Hours)
Activate Incident Response and Disaster Recovery Plans. Contain the breach, isolate affected systems, and preserve forensic evidence.
Open a CAPA within the QMS to formally record the event, date, and impact.
Coordinate Communications. Notify regulators (FDA, HIPAA, GDPR, FTC) and clients promptly and factually, with no speculation.
Internal Briefing. Guide employees on communication protocols to avoid misinformation.
🔍 2. Investigation and Root Cause Analysis
Engage a Digital Forensics and Incident Response (DFIR) team to identify the attack vector (phishing, zero-day, vendor compromise).
Determine which systems, devices, or patient data were affected.
Use structured methods such as the 5 Whys or a Fishbone diagram to isolate the true root cause.
🧩 3. Risk Assessment and Patient Safety Review
Update your ISO 14971 Risk Management File with new cybersecurity hazards.
Evaluate impacts on device performance, essential functions, and patient safety.
Document findings in postmarket surveillance (PMS) records.
🛠️ 4. Corrective Actions and Remediation
Root Cause Remediation: Eliminate malware, close exploited vulnerabilities, revalidate affected firmware or software with regulatory approval.
Infrastructure Hardening: Conduct a full security audit, apply patches, enforce Zero Trust segmentation, and require MFA for all privileged access.
Enhance Monitoring: Deploy Endpoint Detection and Response (EDR) and Security Information and Event Management (SIEM) for continuous vigilance.
🔄 5. Secure Development and Prevention
Implement Secure Software Development Lifecycle (SSDLC) practices aligned with AAMI TIR57 and NIST 800-218 (SSDF).
Introduce threat modeling, secure coding, code signing, and data encryption for all new devices.
Integrate security verification steps in your design and development controls.
Train engineers, QA, and field staff on handling cybersecurity incidents with urgency and accuracy.
🧠 6. Strengthen Incident Response and Disaster Recovery
Formalize and test your Incident Response Plan (IRP) and Disaster Recovery Plan (DRP) quarterly.
Conduct tabletop exercises involving IT, QA/RA, and senior management.
Include cybersecurity events in your business continuity planning (BCP).
Maintain logs and audit trails for FDA and client review.
📋 7. Verification of Effectiveness and CAPA Closure
Validate that all corrective actions have resolved the root cause and that preventive measures are in place.
Record outcomes, evidence, and verification results in the CAPA record.
Keep documentation audit-ready for FDA inspections.
🧾 8. Postmarket Surveillance and Regulatory Reporting
Expand PMS to include cybersecurity metrics (vulnerability management, patch timeliness, incident recurrence).
Report significant breaches to FDA within 30 days (or 5 days if patient safety was at risk).
If device safety was impacted, issue a Field Safety Notice (FSN) or correction/removal notice as per 21 CFR 806.
🤝 9. Rebuilding Trust with Hospitals and Regulators
Transparency First: Clearly communicate what happened, what was affected, and what’s been done.
Independent Validation: Use a third-party assessor (UL, HITRUST, ISO 27001) to verify improvements.
Ongoing Collaboration: Form a Cybersecurity Advisory Board with hospital IT and clinical engineering partners.
Patient Safety Messaging: Lead with empathy and clarity; reinforce that safety remains your top priority.
🧭 10. Long-Term Strategy: Making Security a Core Value
Adopt a Security by Design philosophy across your product portfolio.
Integrate cybersecurity checkpoints into design reviews and supplier management.
Maintain cyber insurance and rehearse BCP and DR plans regularly.
Build a feedback loop; every breach response improves the next generation of devices.
🔒 Final Thoughts
Cybersecurity in medical devices is not just about compliance; it’s about preserving trust. A transparent, well-documented, and proactive response can transform a breach from a reputational crisis into a demonstration of resilience and leadership.
Recent Cybersecurity Incident: Oxford Nanopore MinKNOW (CISA, October 2025)
CISA reported multiple high-severity vulnerabilities in Oxford Nanopore Technologies’ MinKNOW sequencing platform (CVSS v4 score 8.3), including missing authentication, insecure credential storage, and improper handling of temporary files. These flaws could allow remote attackers to disrupt sequencing operations, exfiltrate or alter data, and bypass authentication controls. Oxford Nanopore has released updates in version 24.11 to address the issues and advises users to disable Remote Connect unless necessary, apply endpoint protection, and isolate sequencing systems within secure network environments.

Comments