Managing Cybersecurity as a CAPA Event: 5 Steps to Handle Risks Effectively
- Rajesh Kanungo
- Nov 25, 2025
- 4 min read
Cybersecurity incidents are increasingly recognised as quality and compliance events that can affect the entire organisation, rather than being limited to the IT department. Because a single vulnerability could disrupt operations, compromise product integrity, or lead to regulatory noncompliance, cybersecurity issues must be handled with the same rigor as other CAPA events.
When an organisation combines cybersecurity risk management (AAMI TIR57:2016 (R2023)) with safety and operational risk management (ISO 14971:2019), it gets a complete picture of risks, which allows it to respond more quickly, mitigate more effectively, and prevent for a more extended period of time. Moreover, this combination of measures guarantees that all operations undertaken can be monitored and are traceable, a very important condition for regulatory and compliance supervision.
The guide below explains the process for handling cybersecurity incidents as CAPA events in a controlled manner, helping teams respond in an orderly fashion and maintain operational quality and compliance.
1. Identify Cybersecurity Incidents That Necessitate CAPA
It is not necessary to involve the CAPA department in every technical or IT-related problem. The primary focus should be on security incidents that actually have a quality, operational, or compliance impact. Some of the main signals that a cybersecurity event should be dealt with through the CAPA process are cases that:
Compromise operational or product quality: Problems that could affect the reliability, performance, or integrity of products, services, or processes.
Create systemic process or workflow gaps: Exposure to internal control weaknesses, procedures, supply chain, or operational systems due to vulnerabilities.
Trigger regulatory or compliance concerns: Glitches that may lead to noncompliance with industry regulations, standards, or contractual requirements.
After determining the incident, it is very important to record the time, place, and source of discovery, as well as the potential impact, without delay. Initial documentation serves as a traceable record for compliance purposes and gives management the opportunity to evaluate the risk, decide on the actions to be taken, and allocate resources in an efficient manner.
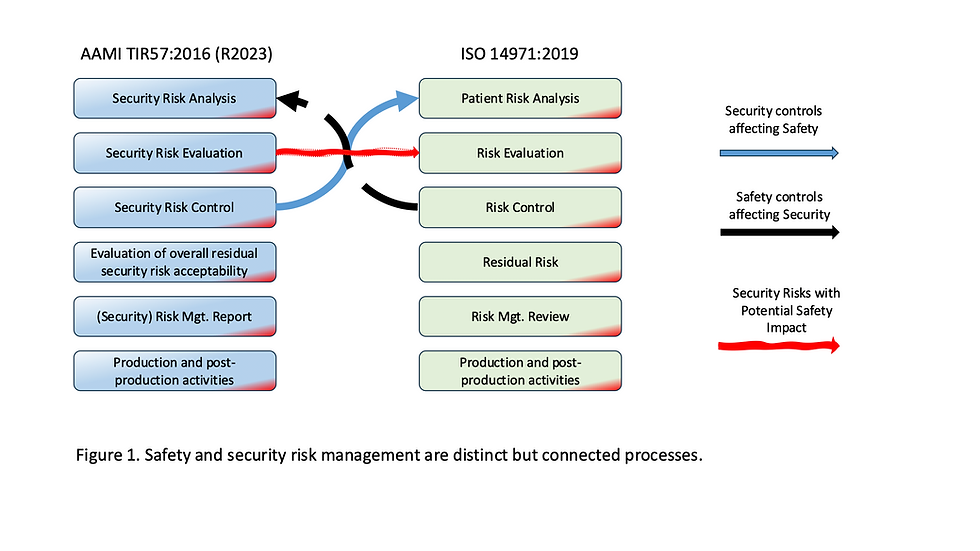
2. Connect Cybersecurity and Safety Risks
The integration of cybersecurity and safety risks has been a trend that has been going on for a long time. The failure of your equipment may not only damage the data or the process but could also result in the destruction of the product, the process, or the stakeholders.
Management-level executives should confirm that security threats are scrutinised using AAMI TIR-57 and that safety and operational risks are evaluated using ISO 14971. Where a cybersecurity loophole inflicts operational or safety issues, the organisation should document it comprehensively in the risk management files.
In addition, executives’ attention to both security (confidentiality, integrity, availability) and safety (potential harm to operations, users, or stakeholders) risks gives them a more detailed picture of the risks faced by the whole organisation. Besides, this agreement supports informed decision-making, regulatory compliance, and economic prioritisation of resources, which is a guarantee that the risks that come in both the short and long term are handled.
3. Conduct Thorough Investigations
CAPA cannot function without the part that emphasizes investigating the cause of an incident and understanding its impact on the entire operations or compliance. Consequently, detailed inquiries provide management with an understanding of the origin, structural weaknesses, and potential paths for process changes.
Probe should cover:
System or software vulnerabilities: Any faults or incorrect settings that contributed to the occurrence of the incident.
Supplier or third-party components: External vendors or partners with weaknesses that may expose the company to risk.
Potential exploitation routes: Operations or procedures that are lacking and can be used to get unauthorised access to systems or processes.
It is beyond the power of a single department to achieve this. The respective teams of security, quality, operations, and compliance should synchronise their work to ensure thorough scrutiny and to ensure that senior management receives a brief, actionable report that facilitates their strategic decision-making.
4. Implement Corrective and Preventive Actions
Where the causes of failure have been unmasked, CAPA should involve not only the actual containment of the situation but also future prevention. Such actions may comprise:
Separating the systems or components that are affected from the rest in order to stop the negative impact from spreading.
Installing software updates, patches, or security settings
Changing standard operating procedures (SOPs) and security measures so that the situation will not be repeated.
Enhancing supplier management or internal process control.
Besides, management has to do everything in its power to ensure that all steps are effective and that the CAPA documents are linked to risk management files. It is through this that control is being kept and the necessary audit, regulatory, and strategic reporting evidences are provided.
5. Monitor, Verify, and Close the Loop
A corrected action, along with a preventive one, will be regarded as an accomplishment only when the measures it suggested are verified as successful. In cybersecurity terms, it means there is a need to have continuous monitoring, post-event surveillance, and trend analysis in order to be able to find new threats or vulnerabilities.
Executives will be able to achieve these objectives by monitoring incident metrics and carrying out regular reviews of the trends over time:
Renew continuous improvement projects.
Reduce operational and compliance risks.
Present to regulators and stakeholders a good proactive governance.
By closing the loop through measurable outcomes, organisations can transform cybersecurity incidents into a weapon. Such incidents become an organisation’s opportunities to deepen resilience, comply with the regulations, and protect the organisation's reputation rather than being threats.
Strategic Takeaways and Looking at the Big Picture
Cybersecurity problems should not be treated as isolated incidents handled solely by the IT department. They represent strategic quality and compliance challenges that require the involvement of the top management. Organisations, by integrating cybersecurity risk management (TIR-57) with safety and operational risk frameworks (ISO 14971) via CAPA, can respond decisively, thereby preventing recurrence and deepening their resilience.
A successful CAPA system transforms forced situations into developmental opportunities, enabling the management team to ensure the organisation's functioning, fulfil requirements, and maintain stakeholder trust. On the other hand, if teams want to strengthen their cybersecurity and compliance strategies, they can find resources like Talasecure helpful for monitoring, risk management, and proactive governance.

Comments